Welcome to Security Bot’s documentation!
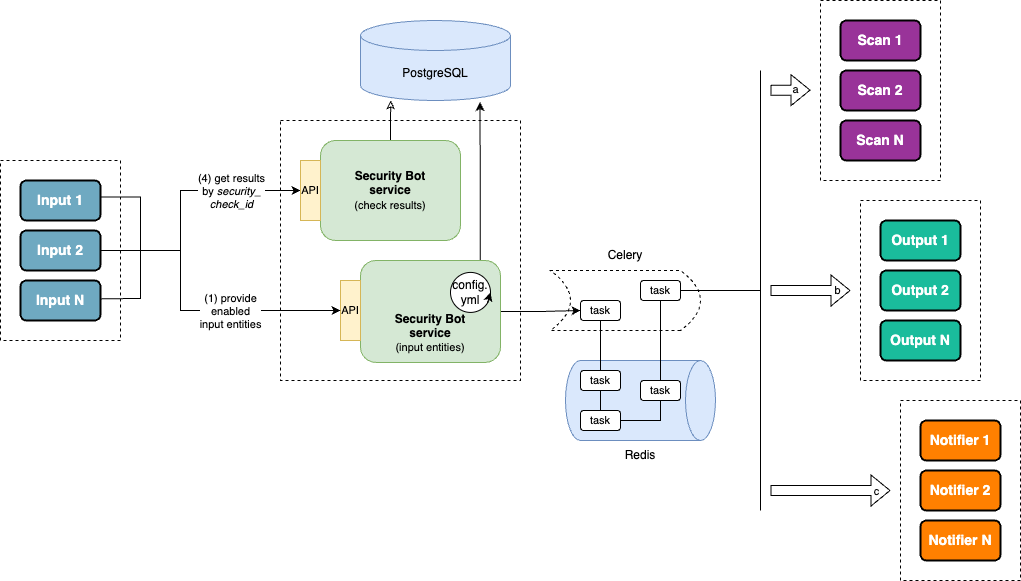
The Security Bot (SecBot) is an orchestration service designed to communicate with various external units (see the following scheme) to detect security-related issues in developers’ code. It can be implemented as an extra pipeline stage to be passed (along with linting, unit-tests, and build) or used in any other way.
In its work, this service
receives from development and distribution platforms (“Inputs”) information on changes that a software engineer contributes (“input entity”)
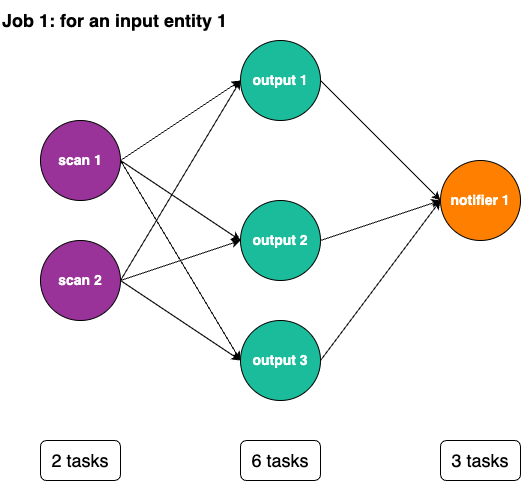
based on its configuration and the input entity’s type, draws up a processing plan (“job”; see an example of it later)
according to this plan, creates a necessary number of tasks for different units to be successively performed to
scan the input entity with code analysis tools (“Scans”)
aggregate the found security issues from Scans, merge duplicates, and do other relevant things with defect management systems (“Outputs”)
inform the interested parties of the results by means of instant messaging (“Notifiers”)
provides the “Input” platforms with the check results (status) on request. (Based on this status—“success” or “fail”—the changes being contributed are allowed or blocked.)
Note
As the scheme suggests, SecBot is split into two instances running in separate containers to ensure high availability and distribute the load. One instance is responsible for receiving requests to process data, whereas the other is dedicated to providing the results of this processing.
The following example of a processing plan, presented as a graph, implies that SecBot’s job is configured to use two Scans, three Outputs, and one Notifier. The overall number of tasks is 11.